Post Processor Encryption
POST PROCESSOR ENCRYPTION
When creating a customized post processor, many hours can be spent on completing the required modifications. Because of this time spent, or for reasons of confidentiality, protecting the logic in the post processor becomes important.
The BobCAD-CAM Development Team has created a utility in the software that allows anyone to define sections of, or an entire post processor to be encrypted, thus protecting the logic and settings. This utility can be found in the Help menu in your BobCAD-CAM software.
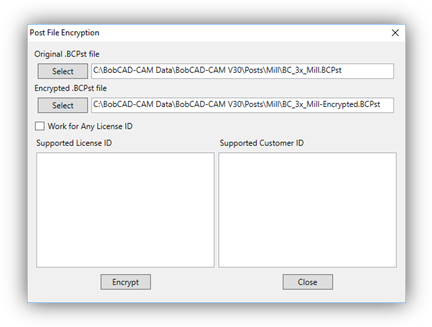
The BobCAD-CAM Post File Encryption utility scans the *.BCPst post processor file for special markers, and encrypts the Post Lines that exist between them.
There are 2 main functions of the Post File Encryption utility.
- Encrypt the posting logic to not allow others to see how it is setup or any formulas used.
- Define specific License and Customer IDs allowed to use the post processor file.
IMPORTANT NOTE: Once the post processor file has been encrypted the action cannot be undone! You must retain a copy of the original post processor file. Failure to do so will eliminate your ability to ever get back to the encrypted sections of the post processor.
Post Encryption Special Notes
The Post File Encryption utility uses special markers in the *.BCPst file to indicate the sections that are to be encrypted. These markers can be seen below:
<--BEGIN ENCRYPT This marker indicates the beginning of where the utility should start encrypting the Post Lines.
<--END ENCRYPT This marker indicates the ending of where the utility should stop encrypting the Post Lines.
The posting engine supports defining multiple sections of the post processor to be encrypted. Special considerations should be made when choosing where to put the Start and End markers into the post processor.
- Every <--START ENCRYPT marker in the post processor must contain a paired <--END ENCRYPT marker.
- You should NOT include previously encrypted sections between your Start and End markers.
Example Start and End markers in a Post Processor:
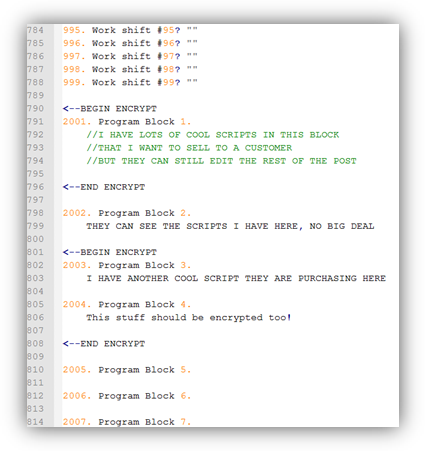
The result of the above markers results in the following output post processor file:

No Markers in Post Processor File
When using the Post File Encryption Utility on a Post Processor that has NO Start and End markers found the utility will then encrypt the entire post processor.
How to Use the Post File Encryption Utility
1. Edit your post processor file to include the <--START ENCRYPTION and <--END ENCRYPTION markers.
2. Make a backup copy of your post processor saved in a SAFE location.
3. Launch the Post File Encryption Utility from the software Help menu.
4. Select the Original *.BCPst file you wish to encrypt.
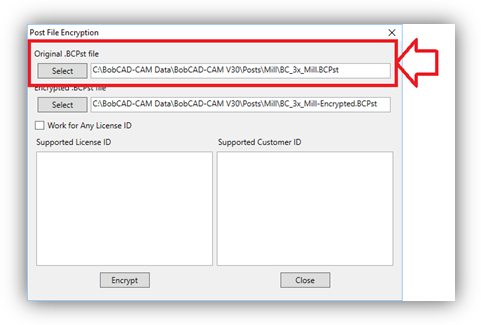
- Select, or Type the name of the NEW post processor the utility should create.
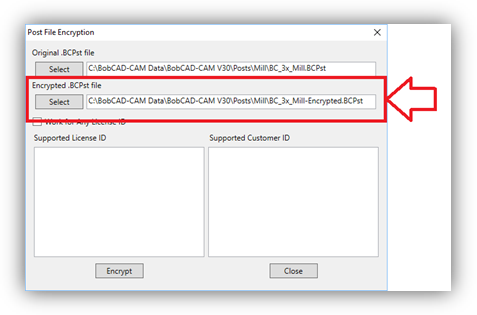
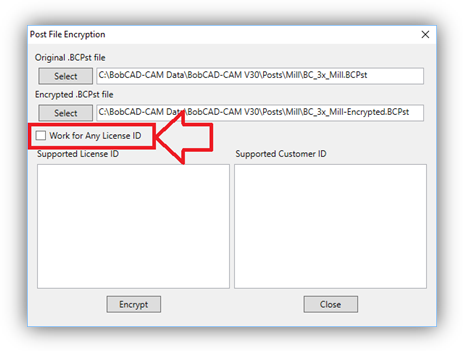
6. If you wish the post processor to work for all License and Customer IDs the check the Work For Any License ID checkbox.
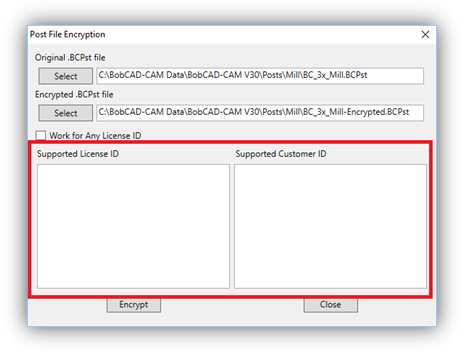
7. If you wish to define specific License or Customer IDs the post processor should work with specify the IDs in the Supported License ID or Supported Customer ID fields.
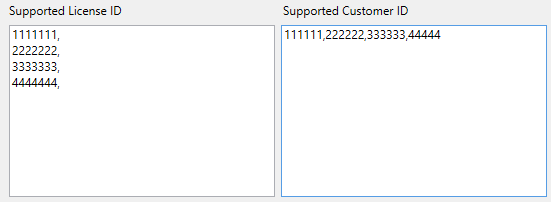
NOTE: The License ID or Customer ID numbers entered must be separated with a “,” character. Both methods shown below are acceptable:
-
1111,2222,3333
-
1111,
2222,
3333,
8. Click the Encrypt button and the post processor file will be encrypted.








